The $235 million hack of Indian cryptocurrency exchange WazirX, suspected to involve North Korean hackers, has significant implications for India’s crypto industry
The significant $235 million breach of the Indian cryptocurrency exchange WazirX on July 18 has prompted serious concerns regarding the security of exchanges and the future of cryptocurrency in India.
Web3 security firm Cyvers was among the first to detect “multiple suspicious transactions” involving WazirX’s “Safe Multisig” wallet on Ethereum as the attack unfolded with alarming speed and precision.
The attacker transferred a staggering $234.9 million in funds to a new address, with the caller of each transaction being financed with assets from cryptocurrency mixer Tornado Cash.
The attacker promptly converted the stolen funds into Ether to obscure the trail of stolen funds, which included a diverse selection of cryptocurrencies such as Pepe, Gala, and Tether.
The exchange’s wallet also contained smaller quantities of other tokens and approximately $100 million in Shiba Inu, $52 million in ETH, and $11 million in Polygon’s MATIC.
WazirX promptly suspended withdrawals of cryptocurrencies and Indian rupees on the platform in response to the security breach. The exchange also disclosed that it was “actively investigating the incident.”
When contacted by Cointelegraph regarding the circumstance, Rajagopal Menon, a spokesperson for WazirX, stated, “We are unable to provide statements to the press at this time.” Our Twitter account provides updates.

The future of the crypto sector in India
The breach could significantly affect the cryptocurrency sector in India, which has thrived despite government pressure.
Utkarsh Tiwari, the chief strategy officer of KoinBX, an Indian cryptocurrency exchange, stated to Cointelegraph that a security compromise of this magnitude is certain to elicit apprehension due to its potential impact on a variety of stakeholders in the crypto ecosystem, such as retail investors and other exchanges. Additionally, he stated:
“Under India’s G20 presidency, we have seen our government push for comprehensive and standardized regulations for all global Virtual Assets Service Providers. Furthermore, historically, we have seen the Indian government always prioritize investor protection above all else.”
Consequently, Tiwari anticipates that Indian digital asset exchanges will allocate more resources to sophisticated security infrastructure. He thinks this will demonstrate the resilience and innovation of the Indian digital asset market and community.
India’s crypto industry is anticipating potential respite from the country’s stringent crypto tax regulations.
Recent: Elon Musk criticizes the European Union for its “illegal” free speech agreement
The India Finance Minister, Nirmala Sitharaman, is scheduled to deliver the Union Budget for the upcoming fiscal year on July 23, and the crypto sector anticipates favorable modifications.
India has implemented one of the most stringent tax regimes on cryptocurrency since 2022, levying a uniform 30% capital gains tax on profits from digital assets, including non-fungible tokens. Furthermore, a 1% tax on crypto transactions is deducted at the source (TDS).
Sumit Gupta, CEO of the Indian exchange CoinDCX, has been advocating for a reduction in the TDS rate to 0.01% in the upcoming budget, as these tax measures have substantially impacted Indian crypto exchanges.
How the attackers gained access to WazirX
Meir Dolev, the co-founder and chief technology officer of Web3 security firm Cyvers, informed Cointelegraph that, even though the exploited vulnerability remains unknown, several significant facts have been revealed since the event.
Initially, he observed that WazirX employs a multi-sig wallet that necessitates four signatures to effectuate a transaction. The exchange also employs Liminal as a custody provider, ensuring the final signature is included in each transaction. Finally, WazirX’s wallet has a whitelist policy, which restricts the number of wallets to which it can send funds.
According to Dolev, the assault vector consisted of two distinct addresses: the first address initiated the transaction, while the second address received the funds. He found his wallet via Tornado Cash to pay petrol fees as the individual who initiated the transaction.
“Eight days before the attack, the hacker also deployed a malicious contract that was later used to change the implementation of the WazirX wallet.”
He also clarified that the attacker could modify the implementation of their multi-sig wallet to his malevolent contract just a few minutes before the first exploit transaction by utilizing the signatures of WazirX and Liminal custody.
“He was able to execute any transaction without the need for WazirX or Liminal to sign on the transaction from that point forward,” he emphasized.
Dolev posited that the attacker may have compromised WazirX endpoints or laptops to obtain the requisite signatures, potentially by utilizing a user interface (UI) hijack on Liminal’s behalf.
He stated that WazirX may have believed it was signing a legitimate transaction, and this is the impression it formed based on the UI, which was potentially under the hacker’s control.
Liminal Custody has maintained that its platform is secure, even though preliminary investigations indicate that one of the self-custody multi-sig smart contract wallets created outside the Liminal ecosystem was compromised. “We can confirm that Liminal’s platform is not breached, and Liminal’s infrastructure, wallets, and assets remain safe,” says the company.
Suspected North Korean involvement
Several analysts think North Korean hackers may be accountable for the incident, complicating an intricate situation.
Elliptic, a blockchain forensics firm, previously informed Cointelegraph that the data pointed to North Korean involvement. They explained, “The North Korea attribution is based on analysis of the on-chain transactional behavior and other information.” Specific patterns and techniques characterize this style of actor.
ZachXBT concurred with this sentiment, asserting that the breach bears the potential characteristics of a Lazarus Group attack. The Lazarus Group is a notorious North Korean criminal organization with a long history of cybercrime.
Lazarus has been responsible for several of the industry’s most significant exploits, such as the $600 million Ronin Bridge incident, and has terrorized the crypto space since 2017.
Additionally, the cryptocurrency market encountered substantial volatility during the aftermath of the breach. The breach resulted in the theft of over $100 million in SHIB tokens, which caused a 10% decline in the price of the popular memecoin.
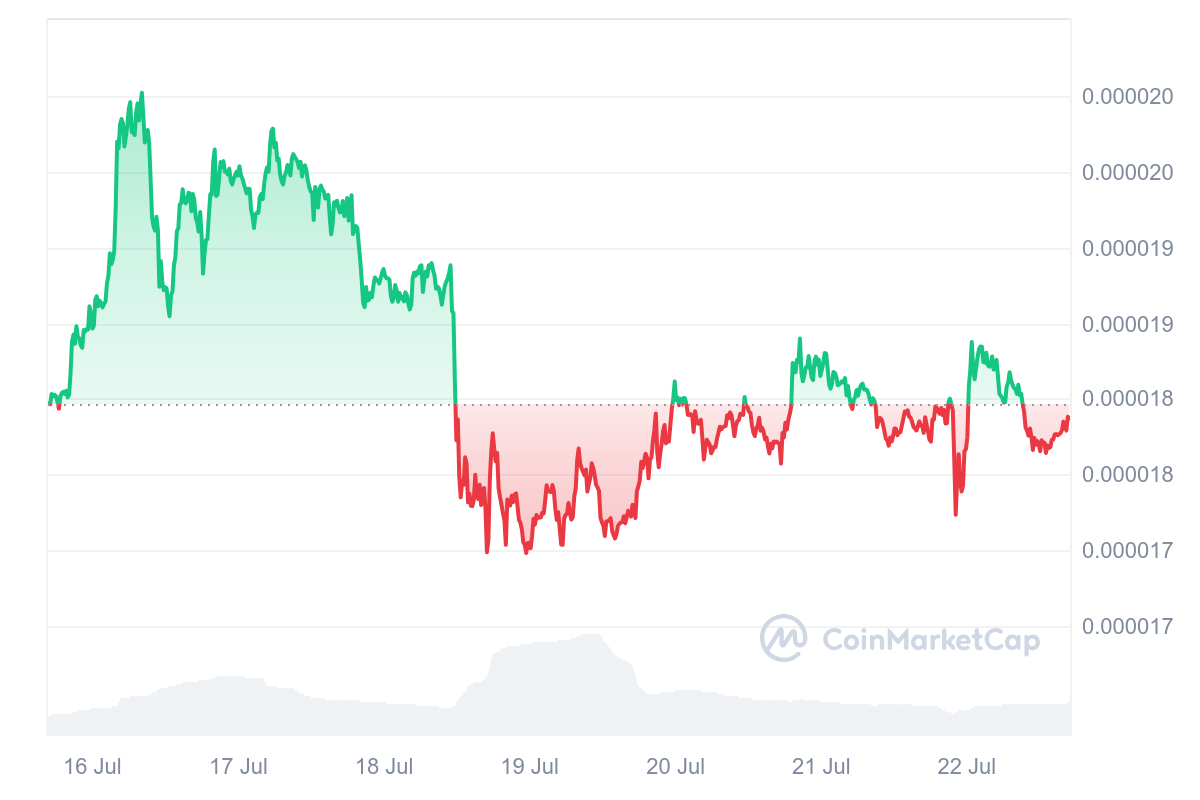
On July 19, the blockchain analysis platform Lookonchain reported that the attackers had already begun trading SHIB assets for ETH, selling 35 billion SHIB tokens valued at $618,000. This occurred one day after the breach.
The exploiter had exchanged most assets for 43,800 ETH ($149.46 million) and held 59,097 ETH ($201.67 million).
WazirX has promptly implemented measures to mitigate the impact and retrieve the misappropriated funds. The exchange is pursuing additional legal actions and has submitted an official police complaint.
The Financial Intelligence Unit and the Indian Computer Emergency Response Team have been informed of the incident, and it is currently contacting more than 500 exchanges to block the identified addresses.
The exchange declared, “We are actively collaborating with numerous exchanges to develop supplementary resources to support our recovery efforts.”
