A 24-year-old hacker accessed over 100 million people’s data after breaking into AT&T networks. Data decentralization may reduce such threats in the future.
Something is wrong with data security when a 24-year-old American living in Turkey can get into not one but two of the country’s most extensive communication networks while everyone else is asleep.
In the most recent AT&T attack, more than 100 million AT&T users’ calls and messages were stolen. The hacker showed how a reverse-lookup tool could readily link the call and text message metadata to the names of family members, coworkers, and, in some circumstances, a user’s general position and movements, even though the stolen files contained no text content or personal information. AT&T refrained from apologizing, instead expressing sadness for the event and tactfully mentioning that the FBI and Department of Justice took two months to reveal the data leak.
AT&T is just one of several companies that promote “cyber resilience,” a catchphrase approach that indicates how well a business or government body can foresee, withstand, recover from, and adjust to cyberattacks. The AT&T fiasco shows the sharp increase in cyberattacks over the previous year, making the phrase synonymous with embarrassing system flaws.
Specific experts have come to terms with the ongoing breaches that are currently occurring, arguing that cyberattacks are unavoidable and that a prevention-focused approach should give way to one that emphasizes cyber resilience. This passive strategy keeps organizations afloat and profitable but accomplishes little to solve the most pressing problem—protecting Americans’ sensitive personal information.
The United States needs to rethink data security completely. While it’s crucial to have backup plans and resources ready to recover after a breach or other digital disaster, it’s also necessary to take a different strategy emphasizing decentralizing data ownership and governance from the start. An individual’s right to manage, preserve, and profit from their digital imprint is referred to by this strategy, which is also known as digital sovereignty.
There are two essential reasons why data sovereignty should concern Americans. Firstly, regaining ownership of one’s digital assets may allow people to profit from their information. Regaining this economic autonomy would change the “asymmetrical marketplace,” where people have very little knowledge of the value and uses of their information compared to the businesses that steal and profit from it and transfer power away from the few “data monarchs” who control a large portion of the world’s information.
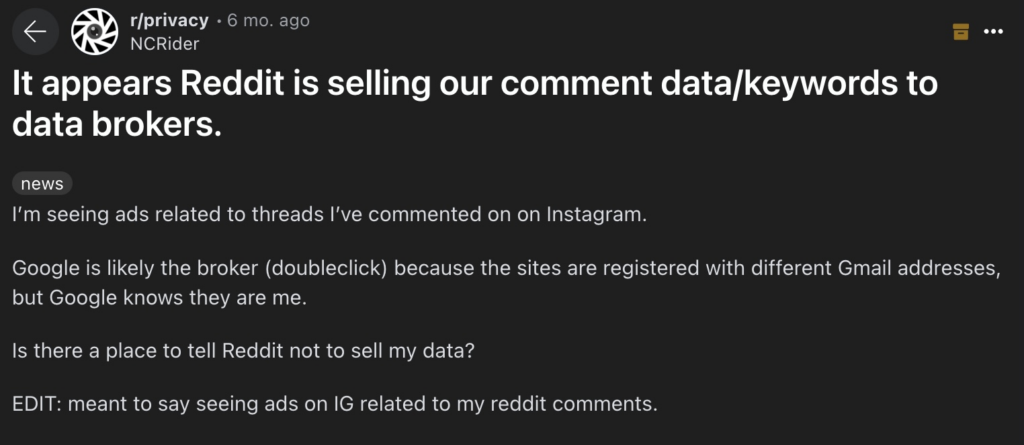
This disparity has been made worse by artificial intelligence (AI). Without the consent of or payment to technology users, the race to consume as much information as possible has further distorted this opaque market to the few data monarchs’ advantage. For example, the social media site Reddit intends to sell user comments to Google and other businesses for over $200 million to fund artificial intelligence initiatives. Users of Reddit will not get paid and will be unable to sell, broker, or lease their commenting data. However, they ought to.
Americans should be concerned about data sovereignty for another reason: privacy. This issue could significantly affect the 2024 presidential election. If there’s one thing the Cambridge Analytica scandal of 2018 taught us, it’s how influential information, analytics, and political persuasion can be in American electoral politics. Facebook theoretically received agreement from social media users through a contract of adhesion, but no option was offered for consumers to discuss the terms of data usage. In that event, Facebook micro-targeted its users to influence their voting preferences.
Data sovereignty could provide an additional layer of defense to keep people safe from covert political influence and shield American society from unethical actions that sway democratic processes. However, if politicians or American citizens wish to compete for influenceability, it should be on their own terms.
Since data sovereignty is decentralized by nature, it also makes sense to address weak cyber resilience tactics with it. A post-quantum blockchain encryption could be used to ensure individual data control instead of keeping information in a centralized database or the cloud. The need to move toward decentralized data governance is further demonstrated by the recent CrowdStrike software update, which not only caused worldwide system failures but also demonstrated how standardized and interconnected data security software offerings have become, as if the AT&T breach wasn’t enough evidence.
The United States can have its cake and eat it, too. How? To begin with, policymakers and cybersecurity specialists should look into cases where data sovereignty is flourishing. For example, Indigenous people have embraced the self-sovereign concept and are adamantly promoting ownership over their census, health, social services, and environmental statistics. Analyzing how Indigenous communities manage their personal information and exercise data sovereignty can be a case study and possible legislative or technological sandbox for digital economic zones.
Lawmakers should also redouble their efforts to force digital businesses to reveal the worth of the information their users provide, and they should push for new laws that restrict organizations’ capacity to provide usage contracts that eliminate consumers’ bargaining power. A bipartisan legislation attempt that addressed the valuation issue was the DASHBOARD Act, which was introduced in 2019 but has since stagnated. Meanwhile, state privacy rules are becoming more popular, with 18 states passing legislation aimed at being more user-centric. Given that some state legislation, such as the California Consumer Privacy Act (CCPA), allows citizens to refuse to have their personal information sold or shared, it is evident that these efforts are headed in the correct direction.
Ultimately, businesspeople ought to keep experimenting with developing blockchain-based platforms, goods, and services and constructing dispersed, post-quantum, worldwide data spaces intended for people and not-for-profit organizations.
Ultimately, America requires a new security strategy that values autonomy and decentralization while opposing complacency and submission to a small number of influential individuals.