The Lazarus Group, based in North Korea, targets the crypto industry via LinkedIn by enclosing sophisticated malware within job application codes.
The convergence of finance and technology in the contemporary digital era has created a conducive environment for cybercriminals, specifically in the exponentially expanding cryptocurrency industry.
Cybersecurity firms have recently revealed a concerning pattern: organized cybercrime groups are utilizing professional networking platforms such as LinkedIn. In particular, the notorious Lazarus Group has devised a strategy of assault in which they assume the guise of job-seeking computer programmers.
The Lazarus Group of North Korea presents itself as developers on LinkedIn
A researcher at the blockchain security firm SlowMist disclosed on Wednesday, April 24, that the Lazarus Group, based in North Korea, has developed a novel method of attacking businesses. The collective assumes the guise of job candidates who are React and Blockchain technologies experts. They initiate contact with specific organizations through LinkedIn and pose as potential candidates.
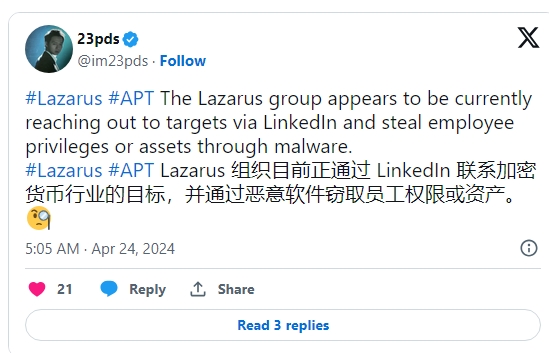
Once communication has been established, they request that the target examine their coding work, which is hosted on platforms such as GitHub. However, the repositories are anything but benign. They comprise malevolent code fragments that, upon being implemented, set in motion a series of occurrences with the intention of infiltrating the target’s computer.
By utilizing this code, the assailants gain covert access to potentially more valuable corporate resources, such as crypto assets and sensitive financial data.
How to Prevent Lazarus Hacking Against Your Organization
The sophisticated strategy employed by The Lazarus Group, which involved disseminating malware via bogus employment offers on LinkedIn, underscores the criticality of heightened vigilance and cybersecurity protocols.
Perform Background Checks: Carefully advise new contacts and prospective employers regarding employment opportunities, particularly if the contact is unsolicited. Utilize LinkedIn to verify the legitimacy of the company profile and mutual connections.
To avoid accepting job offers that require access to code or documents, it is advisable to solicit external validation through recommendations or insights from reputable colleagues or industry networks.
Utilize sandbox settings: Execute any unfamiliar code in a simulation environment isolated from critical systems and data. This precaution allows for the identification of malevolent activities without jeopardizing the integrity of the primary network.
Execute Code Review Methods: Implement a mandatory code review procedure that requires multiple team members to participate before executing any external code within the organization’s systems.
Implement Endpoint Response and Detection (EDR) Systems: Employ sophisticated EDR systems capable of autonomously identifying, isolating, and remediating suspicious activities.
Patch and update systems routinely: Maintaining all software, with particular attention to security tools and browsers, is crucial to applying the most recent security upgrades and updates.
By implementing the strategies above, organizations and individuals can substantially mitigate the likelihood of succumbing to sophisticated cyber-attacks via LinkedIn and other professional networking platforms.
At the Reverse
The Lazarus Group, which the North Korean government supports, has been implicated in several prominent cyberattacks, including the Coinspaid, Atomic Wallet, and Harmony Hacks.
After U.S. authorities sanctioned the Tornado Cash processor, Lazarus Group shifted its focus to alternative services.
Reasons Why This Is Important
The Lazarus Group’s attacks on LinkedIn serve as a sobering reminder of the susceptibilities and potential repercussions of security intrusions. These include monetary setbacks, confidential data compromise, and harm to one’s reputation and trust.