Avalanche and Blockaid have announced a collaboration to include security measures in Avalanche’s Core wallet, the main wallet of the blockchain network.
The security integration checks for increasingly complex phishing scams and exploits that affect Web3 users using Blockaid’s threats database.
The security update prescreens transactions against Blockaid’s database of known malicious threats. It notifies the user of the danger before the transaction is signed and posted to thwart the increasingly sophisticated phishing scams and hacks that plague decentralized finance. Transaction simulation is the name given to this kind of security feature.
Blockaid states that its security system is being utilized to protect products from OpenSea, MetaMask, Zerion, Coinbase, and Rainbow and has assisted in thwarting 1.3 million attacks.
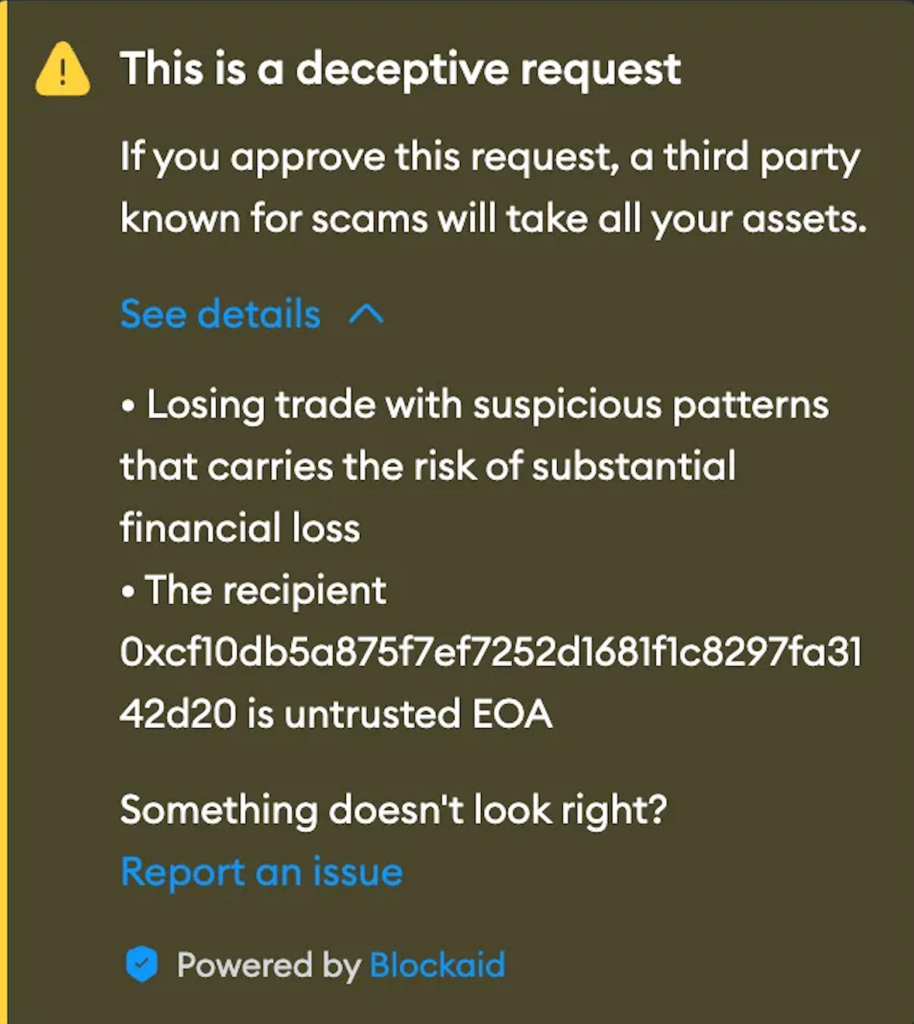
Following the partnership, Ava Labs’ head of consumer products, Akash Gupta, stated:
“This collaboration between Avalanche and Blockaid signifies a significant step forward in providing users security and control without compromising speed and ease of use. By integrating advanced security solutions across the Core suite, we ensure users can explore the Avalanche ecosystem and beyond with peace of mind.”
Critics of Blockaid counter that this is a feature rather than a defect of their security software, arguing that the security screening capabilities cause an excessive number of false positives.
The security company’s spokespeople clarified that an excessive number of false positives is preferable to lowering screening standards and giving bad actors more opportunities to exploit vulnerabilities to further their illegal activity.
In the cat-and-mouse game of cybersecurity, there is also a dynamic threat landscape that can keep one step ahead of transaction simulators.
Cybersecurity expert Bernhard Mueller claims that transaction simulators like Blockaid, WalletGuard, and Pocket Universe may be vulnerable to malware like the notorious “Angel Drainer.”
Mueller clarified that although the effectiveness of these strategies was not assured or failsafe, Angel Drainer might be able to elude transaction simulators by generating dynamic, “unmarked” contract addresses and trying to steal money via those addresses.
The white hat hacker acknowledged that despite his experiments employing the dynamic, unmarked technique, Blockaid could still flag the transaction as suspicious and issue a warning.



