Compound Finance faced a major security breach, compromising its official website. A phishing site now occupies the hijacked domain, posing user risks.
According to Security Advisor Michael Lewellen, the domain theft is unaffected by Compound’s smart contract funds.
According to Compound Labs’ official X account, the business sent out an urgent warning on July 11 at 10:15 a.m., saying,
“The Compound Labs website (compound[.]finance) has been compromised. Please do not visit the website or click any links until further notice”.
The security advisor for Compound, Michael Lewellen, verified the compromise on X and emphasized that customers can utilize something other than the Compound Finance website. Lewellen explained that even though the website has been hacked, all smart contract money is safe, and the Compound protocol is unaffected.
It looks like a clever phishing attack. A fake website intended to steal user data and maybe digital assets has replaced the official Compound Finance website. Known as “domain hijacking,” this assault entails gaining control of a domain name without the owner’s permission, typically through a DNS password compromise.
Through Telegram, blockchain investigator ZachXBT has alerted the cryptocurrency community to the dangers of utilizing the Compound Finance website since it leads to a fraudulent website called compound-finance[.]app.
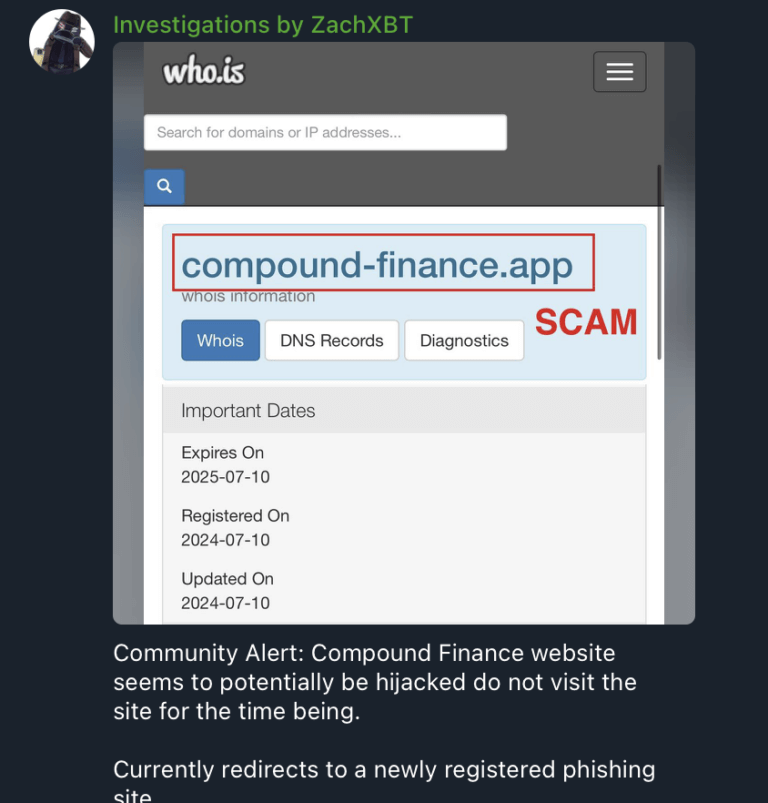
This event came after Compound Finance’s X account was compromised and used to spread a phishing website during the last security breach that occurred last year. It has been revealed that LINK tokens worth about $4.4 million were lost due to that attack.
Until official confirmation is received that the issue has been fixed, the cryptocurrency community is encouraged to proceed cautiously and refrain from dealing with the Compound Finance website. Regarding updates on the situation, users should rely only on official messages from Compound Labs and be on the lookout for any potential phishing attempts.
Web3 security tools and browser plugins can also alert users to potentially harmful links. A few examples are AegisWeb3, Pocket Universe, Wallet Guard, Malwarebytes Browser Guard, and MetaMask transaction insight Snaps.



