Crypto hacker victim gets $153K back in apparent attacker negotiation after a $68M loss in a suspected address poisoning attack.
In what appears to be an act of good faith, the address-poisoning attacker who purportedly duped a user into sending them $68 million worth of Wrapped Bitcoin (WBTC) has returned $153,000 worth of Ether to the victim. The perpetrator sent a message to the victim during the same transaction in which they agreed to negotiate and requested a Telegram username through which they could be reached. The returned sum constitutes a mere 0.225 per cent of the stolen funds.
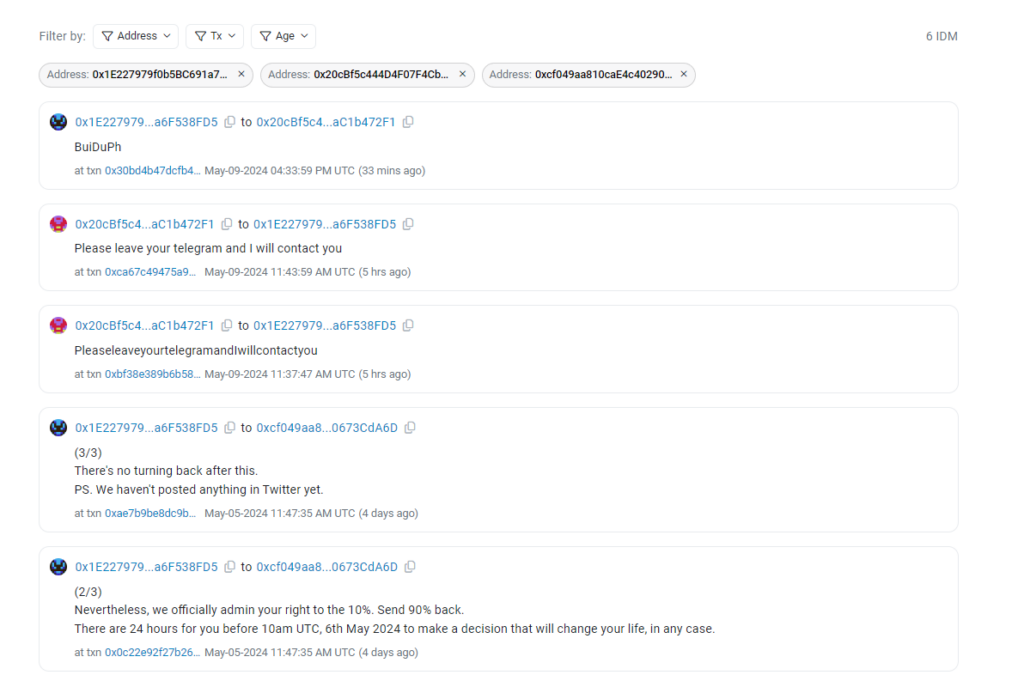
According to blockchain data, the assault victim, whose account concludes in 8fD5, transmitted three messages to an account concluding in dA6D on May 5. Through multiple intermediary accounts, the message’s recipient had obtained funds from the attacking account, which was designated “FakePhishing327990” on Etherscan. This suggests that the perpetrator probably had control over dA6D.
The messages suggested that the recipient would waive legal action against the assailant in exchange for a 10% bounty on the funds, with the condition that the remaining 90% be returned. The victim complained:
“We both know there’s no way to clean this funds. You will be traced. We also both understand the ‘sleep well’ phrase wasn’t about your moral and ethical qualities. Nevertheless, we officially admin your right to the 10%. Send 90% back. There are 24 hours for you before 10am UTC, 6th May 2024 to make a decision that will change your life, in any case.”
On May 9, at 11:37 am UTC, an additional account concluding in 72F1 retaliated to the victim’s message by transferring 51 Ether (ETH), currently valued at $153,000. Additionally, 72F1 had obtained funds from FakePhishing327990 via multiple intermediary accounts, suggesting it was also under the perpetrator’s control.
The perpetrator included the following message in the transaction containing the 51 ETH: “Please terminate your Telegram, and I will get back to you.” They subsequently attempted to rectify their improper punctuation at 11:43 am by publishing an additional message which read, “I will contact you after you leave your telegram.”
The victim replied with a Telegram handle through which they could be reached.
Following an “address poisoning” transaction in which the attacker purportedly duped the victim into inadvertently depositing 1,155 Wrapped Bitcoin (WBTC) (equivalent to $68 million at the time) into their account, negotiations ensued.
At 9:17 am on May 3, according to blockchain data, the perpetrator transferred 0.05 of a token from the victim’s account to their own using a smart contract. Etherscan did not assign a name to the transmitted token; it was merely designated as “ERC-20.” An attacker cannot, in typical situations, transmit a token from another user without obtaining their consent. In this instance, however, the token’s customized design enabled its transfer from an account without the user’s permission.
The victim presumably sent 1,155 WBTC to this address by accident at 10:31 am on the same day. The address might have resembled one the victim might have employed to deposit funds into a centralized exchange or for another reason.
Furthermore, the victim might have perceived that they had previously transmitted a 0.05 token to this address, leading them to conclude that it was secure. Nonetheless, the 0.05 tokens that appeared to have originated from the victim were transmitted by the perpetrator.
Security experts refer to deceiving targets by flooding them with transactions that seem to originate from the targets but are actually the attacker as an “address poisoning attack.” Before confirming a transaction, experts advise users to thoroughly examine the sending address to prevent costly errors caused by these attacks.



