Cado Security Labs warns of AI-made fake sites luring Web3 workers to download malware-infected meeting apps, stealing crypto credentials.
According to Cado Security Labs, Web3 workers are the target of a campaign that employs phony meeting apps to infect websites, apps, and cryptocurrency wallets with malware and steal login credentials.
In a report published on Dec. 6, Tara Gould, threat research lead at Cado, said that scammers are employing artificial intelligence to create and populate websites and social media profiles to look like trustworthy businesses before reaching out to prospective victims to ask them to download a meeting app.
Although the app is called “Meeten,” it is currently known as “Meetio” and undergoes frequent name changes.
Clusee.com, Cuesee, Meeten.gg, Meeten.us, and Meetone.gg have all been used.
After downloading, the app’s Realst info stealer will search for private information to give back to the attackers, including banking card numbers, crypto wallet information, and Telegram login credentials.
Along with information on Ledger, Trezor, and Binance wallets, the hacker can also look for browser cookies and autofill credentials from programs like Google Chrome and Microsoft Edge.
The plan may use social engineering and spoofing. One user claimed that they were exposed as impostors after receiving a message on Telegram from a person they knew who wanted to talk about a business opportunity.
“What’s even more intriguing is that the con artist sent him an investment presentation from the target’s business, which suggests a sophisticated and focused scam,” Gould added.
According to Gould, other people have also claimed: “downloading the software, having their cryptocurrency stolen, and being on calls related to Web3 workers.”
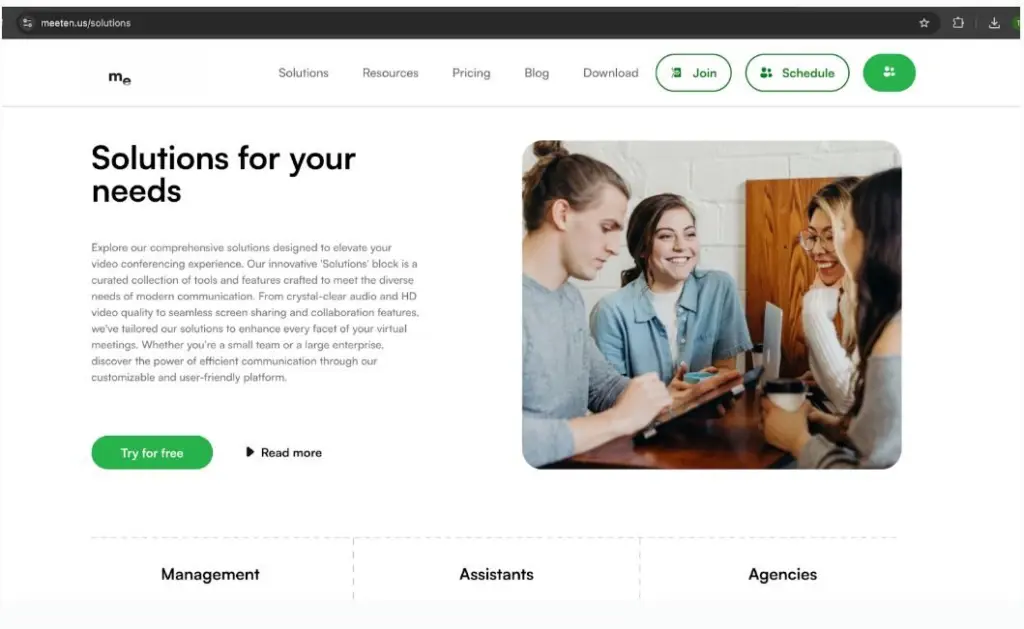
The scammers created a corporate website with AI-generated articles, product information, and related social media profiles, such as X and Medium, to help them appear more credible.
Gould said threat actors are increasingly leveraging AI to develop material for their campaigns despite the fact that most recent attention has been on the technology’s capacity to produce malware.
“By using AI, threat actors can quickly produce realistic website content that gives their scams more legitimacy and makes it harder to identify dubious websites.”
Even before downloading any malware, the phony websites that ask visitors to download the malicious software also employ Javascript to steal cryptocurrency stored in web browsers.
Both a Windows and macOS version have been produced by the crooks. According to Gould, the program has been in operation for almost four months.
These strategies have also been aggressively employed by other con artists.
Onchain investigator ZackXBT claimed to have discovered 21 developers—likely North Koreans—working on a number of cryptocurrency projects employing fictitious identities in August.
The FBI warned in September that North Korean hackers were using malware posing as job offers to target cryptocurrency companies and decentralized finance initiatives.
