A hacker created many deposit receipt tokens on the decentralized finance (DeFi) Delta Prime system, which allowed them to siphon off nearly $6 million.
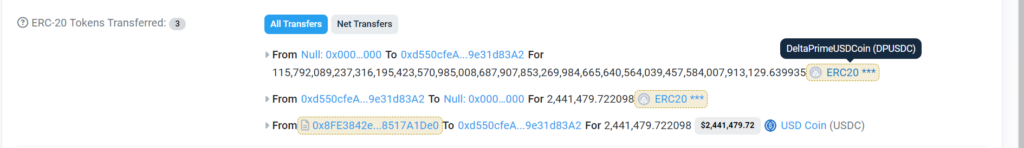
Only $2.4 million of the nearly 115 duovigintillion USDC deposit receipts the exploiter generated were redeemed.
In the first attack, the attacker created more than 115 duovigintillion Delta Prime USD (DPUSDC) tokens, or more than 1.1*10^69 in scientific notation, according to statistics from block explorer Arbiscan.
A deposit receipt for USDC$1.00 stablecoin held at Delta Prime is denoted by the symbol DPUSDC. It is meant to be redeemed for USDC in a 1:1 ratio.
The attacker only burnt 2.4 million of the USDC deposit receipts they had created, earning $2.4 million in USDC stablecoin.
After minting over one duovgintillion Delta Prime Wrapped Bitcoin (DPBTCb), 115 octodecillion Delta Prime Wrapped Ether (DPWETH), 115 octodecillion Delta Prime Arbitrum (DPARB), and numerous other deposit receipt tokens, the attacker repeated these steps for other deposit receipt tokens. Ultimately, the attacker redeemed a small portion of the minted amount to obtain over $1 million in Bitcoin BTC$57,762, Ether ETH$2,284, Arbitrum (ARB), and other tokens.
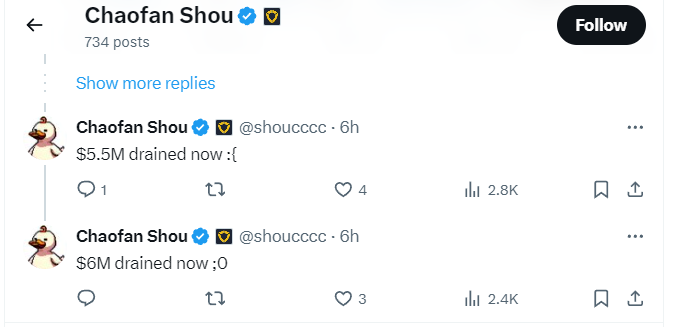
Blockchain security expert Chaofan Shou estimates that the attacker has already taken almost $6 million.
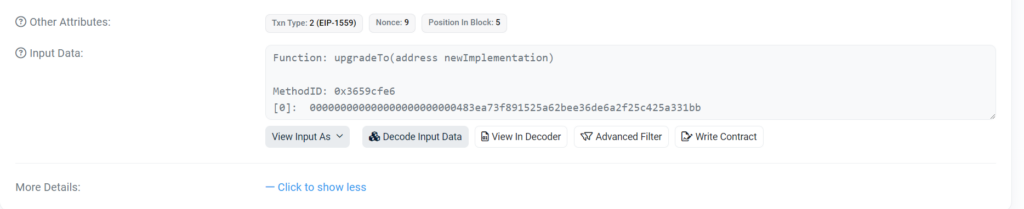
The attacker most likely obtained control of an admin account ending in b1afb by obtaining the developer’s private key, which allowed them to mint these deposit receipt tokens. Using this account, they called an “upgrade” function on every liquidity pool contract in the protocol.
The purpose of these features is to facilitate software upgrades. Setting the proxy point to a new implementation address enables the developer to modify the code within a contract.
However, the attacker pointed each proxy to a fraudulent contract they had written using these functions. The attacker could empty each money pool by minting many deposit receipts through each fraudulent contract.
In an X post, Delta Prime confirmed the incident: “At 6:14 AM CET, DeltaPrime Blue (Arbitrum) was attacked and drained for $5.98 million.”
It asserted that DeltaPrime Blue, the Avalanche version, is impervious to the assault. Additionally, it said that “where possible/necessary,” the protocol’s insurance “will cover any potential losses.”
The Delta Prime assault demonstrates the danger of employing upgradeable contracts in DeFi protocols.
The Web3 ecosystem is meant to stop whole protocols from being exploited by private vital attacks.
In theory, all it would take for an attacker to deplete the protocol is for them to have the private keys of each user. Upgradable contracts, however, bring a centralization risk that could result in the loss of funds for the whole user base.
However, some protocols think that giving up the option to upgrade would be worse than the alternative because it might make it harder for a developer to address flaws discovered after distribution. The question of whether protocols should support updates or not is still being debated by Web3 developers.
Smart contract exploits still put Web3 users at risk. On September 11, an attacker used a code pointing to an unconfirmed function on a different contract to siphon almost $1.4 million from a CUT token liquidity pool.
The Penpie protocol saw the theft of approximately $27 million on September 3, when the attacker was able to register their malicious contract as a token market.



