Without burning the corresponding LP tokens, an account was able to remove 1.4 million BSC-USD through the use of an unreadable function.
A blockchain security platform Certik report states that on September 10, an attacker went through a liquidity pool containing CUT tokens and took roughly $1.4 million worth of Bows Coin Synthetic US Dollar (BSC-USD). The “future yield” element of the CUT token contract was set by another unconfirmed contract, which was also utilized to drain the BSC-USD in an unidentified manner.
CertiK reported the occurrence on X.
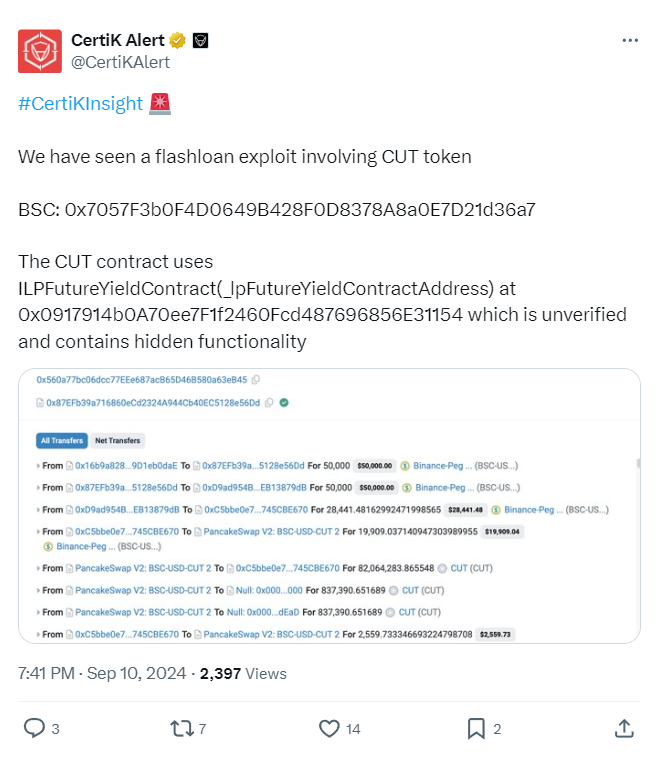
The exploited CUT token may be found on the Binance Smart Chain at an address that ends in 36a7. It is not to be confused with the Crypto Unity project, which uses a different address but the same ticker symbol. The pancake swap exchange included the emptied pool. It doesn’t have impacted any other Pancakeswap pools.
According to blockchain data, the attacker used four transactions to empty the BSC-USD pool. A total of $1,448,974 was subtracted.
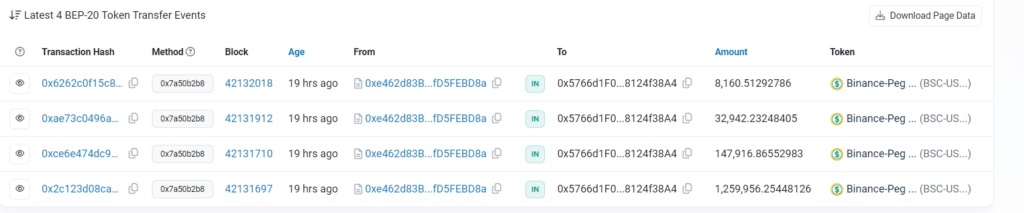
Since the attacker had not previously deposited money into the pool and had no liquidity provider tokens, it seems doubtful that this withdrawal was authorized.
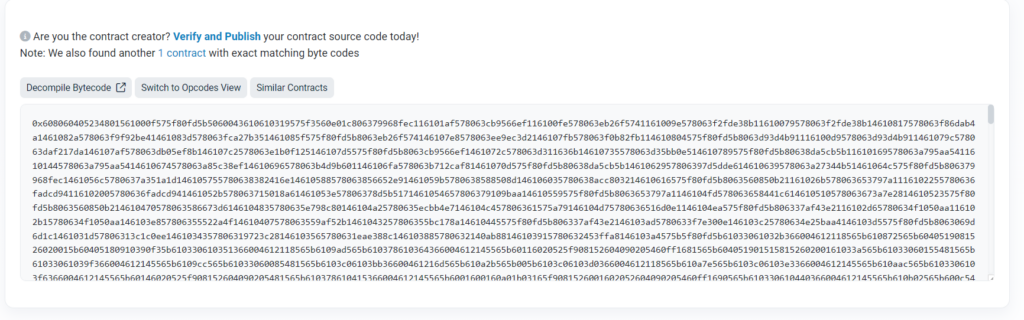
The attacker called a function called “0x7a50b2b8” in each transaction. However, the token contract does not mention it. The report states that this suggests the attacker had to invoke ILPFutureYieldContract(), which allows the user to invoke a different function on an entirely other contract whose address ends in 1154. BSC Scan only reveals an illegible bytecode for this unconfirmed contract.
One significant way that Web3 users lose money is through exploits. On September 3, a Penpie decentralized finance protocol exploit resulted in the loss of nearly $25 million worth of cryptocurrency. On August 6, an attacker used a flawed deployment script to siphon $10 million from the bridge of the Ronin gaming network. In this instance, the exploit has left CUT liquidity providers with a combined loss of $1.4 million.



