Kraken plans to take legal action against security firm CertiK as the “white hat” operation by the security firm turns into a legal blunder.
The Kraken CertiK saga, in which the security firm CertiK claimed to have conducted a white hat operation on specific Kraken accounts (not customers) and withdrawn nearly $3 million (as Kraken claimed), has taken another turn.
The exchange asserted that the total exploited amount was not returned to it, whereas CertiK claims to have returned all funds by their records.
On June 20, CertiK utilized X to provide an update on the situation. They stated that they had returned 734.19215 Ether and 1021.1 Monero, while Kraken requested 155818.4468 Polygon, 907400.1803 USDT, 475.5557871 ETH, and 1089.794737 XMR.
Kraken claims exploit, Certik says white hat operation
Kraken claimed to have received a bug bounty program alert from a purported security researcher on June 9, which marked the beginning of the Kraken-CertiK saga. The alert emphasized a vulnerability in Kraken’s system that enabled users to exaggerate their account balances artificially.
The crypto exchange promptly addressed the issue and identified three accounts that had exploited the vulnerability to withdraw $3 million from the Kraken account.
Kraken discovered that one of the three accounts was a Know Your Customer (KYC) verified account and the account utilized the flaw to credit $4 to their account.
Nick Percoco, the chief security officer of Kraken, stated that this would have been sufficient to establish the bug and claim the bounty. However, the account purportedly shared the flaw with two other accounts within days, resulting in the three accounts earning $3 million from the exchange.
The white hat hacker allegedly refused to entertain the requests and requested the bounty before returning the fund when the crypto exchange requested it after providing the required on-chain proofs.
Kraken did not disclose the identity of the security firm responsible for the “white hat” exploit; however, CertiK disclosed that they were the security firm behind the Kraken exploit.
CertiK asserted that the employee who identified the vulnerability was confronted with returning the stolen funds without providing a wallet address. Cointelegraph was told by Ronghui Gu, co-founder of CertiK:
“The verbal consensus reached during our meeting was not confirmed afterward. Ultimately, they publicly accused us of theft and even directly threatened our employees, which is completely unacceptable.”
According to reports, CertIK transferred the stolen funds to Tornado Cash, a cryptocurrency blending service, to prevent them from being frozen by crypto exchanges. CertiK’s motivations for conducting this “white hat” operation were the subject of considerable criticism from the crypto community.
Crypto community calls out CertiK
The crypto community questioned why CertiK researchers transferred millions of dollars in funds when a single transaction could have demonstrated the vulnerability.
Others reminded them that Tornado Cash is an instrument sanctioned by the Office of Foreign Assets Control (OFAC), and its use could result in legal complications for the security firm. Others inquired whether they intended to return the funds and why they were sent to an OFAC-sanctioned crypto aggregator.
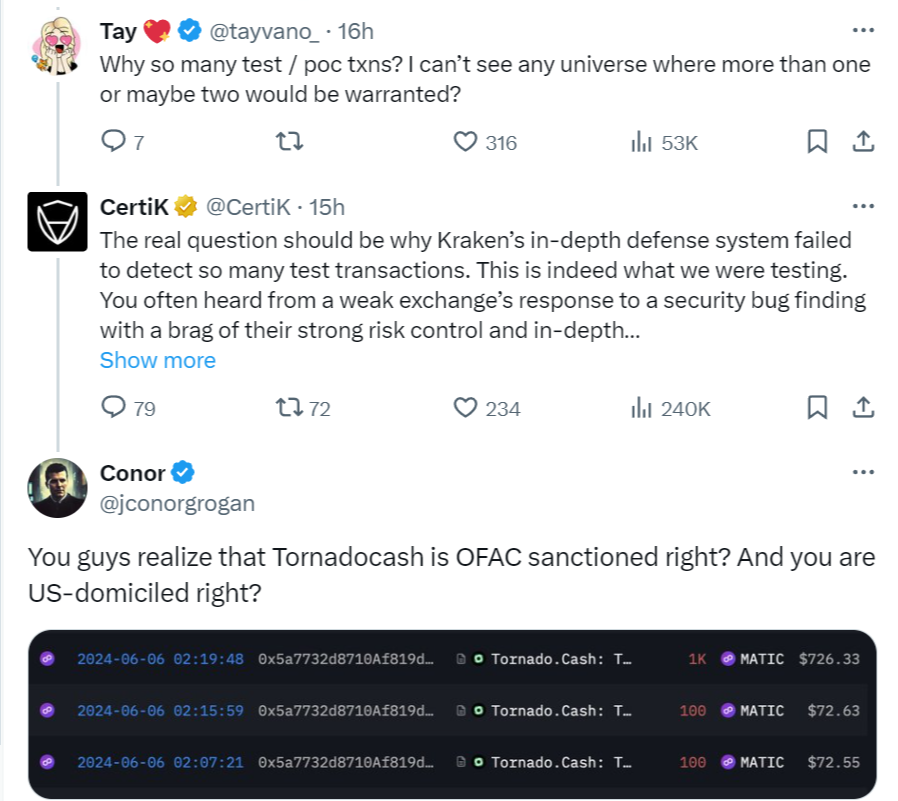
Most crypto communities supported Kraken and denounced CertiK for their evil conduct. Numerous individuals accused them of “stealing” and blackmailed Kraken for the bounty.
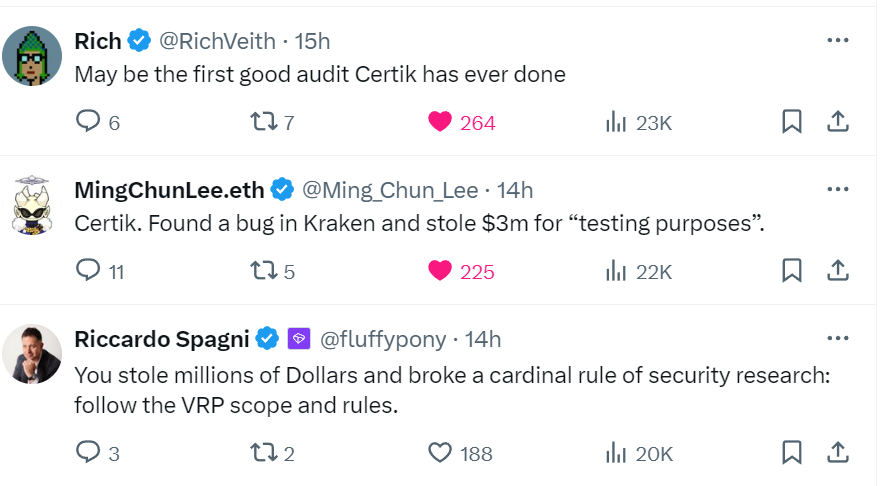
Kraken informed Cointelegraph that they are communicating with law enforcement agencies.



