SlowMist claims that although OKX’s two-factor authentication system was not the primary point of vulnerability, there were two identical phishing events.
SlowMist, a security partner of OKX cryptocurrency exchange, is looking into a multi-million dollar attack that led to the theft of two user accounts.
The subject of the inquiry is the June 9 theft of two OKX exchange accounts via SMS attack, commonly called SIM swapping. SlowMist’s founder, Yu Xian, revealed this knowledge in a post on X.
“The SMS risk notification came from Hong Kong and a new API Key was created (with withdrawal and trading permissions, which is why we suspected a cross-trading intention before, but it seems that it can be ruled out now).”
Although it’s unknown how much was taken in the attack, Xian said that “millions of dollars of assets were stolen.”
2FA did not primarily cause the attack: Slow-Mist
Even if the blockchain security company SlowMist is currently looking into the hacker wallet and related events, the exchange’s two-factor authentication (2FA) systems may not be the primary weak point.
Xian, the founder of SlowMist, wrote the following on June 9 X:
“I haven’t turned on a 2FA authenticator like Google Authenticator, but I’m not sure if this is the key point.”
According to an analysis by Web3 security organization Dilation Effect, OKX’s 2FA system allowed attackers to switch to a low-security verification method, enabling withdrawal addresses via SMS verification.
More experienced hackers, nevertheless, have lately begun evading 2FA authentication procedures. A Chinese trader lost $1 million to a fraud that used the Aggr Google Chrome plugin at the start of June. Hackers utilize stolen user cookies from the plugin to get around 2FA authentication and passwords.
Attacks by phishers are increasing.
June saw increased phishing attempts following CoinGecko’s confirmation of a data breach involving GetResponse, a third-party email management platform. Because of the incident, victims received 23,723 phishing emails from the attacker.
Hackers who use phishing attacks try to obtain private keys to crypto wallets and other sensitive data. Aiming to deceive investors into voluntarily sending money to a phony address that resembles addresses they have previously interacted with, other phishing attempts are also referred to as address poisoning scams.
Because hackers are looking for the easiest targets, private key, and personal data leaks are becoming the leading causes of crypto-related hacks.
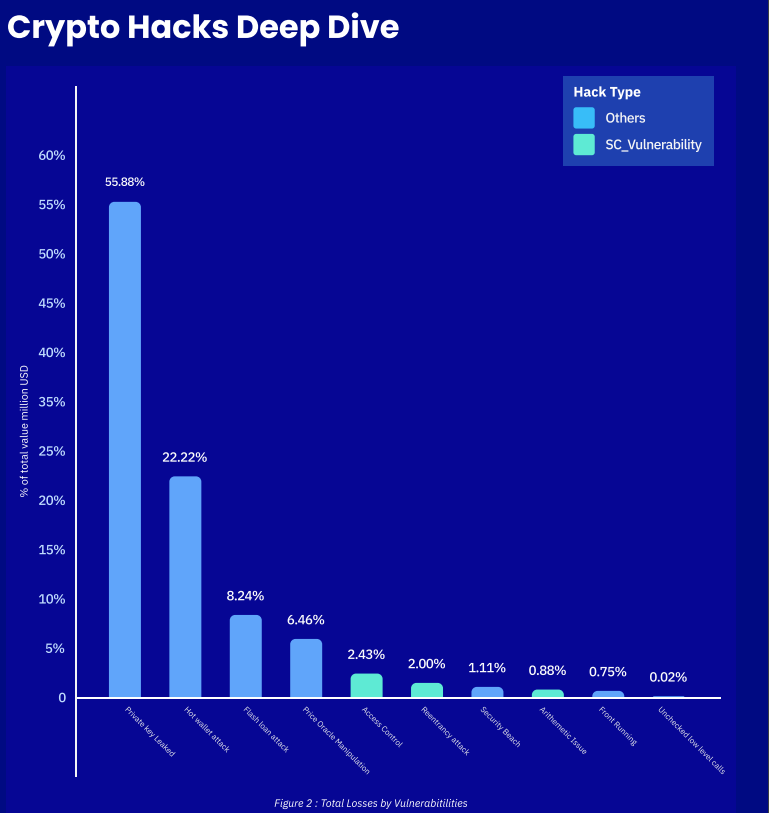
According to Merkle Science’s 2024 HackHub report, private critical leaks during 2023 resulted in the loss of almost 55% of the hacked digital assets.



