Scam Sniffer first warned of Telegram malware scams last December but reports scammers have since adapted tactics to target more victims.
Telegram malware scams have exceeded traditional phishing in volume, rising 2,000% since November, and crypto criminals have made a significant shift to these scams.
The security company Scam Sniffer stated in a Jan. 15 X post that the scams they are seeing are not the “typical connect wallet” type, in which dishonest actors trick a victim into linking their digital wallet to a phony website or platform to steal money.
Instead, scammers are now using phony verification bots in phony alpha, phony trade, and phony airdrop groups to spread sophisticated malware.
According to the company, “They can access your passwords, scan for wallet files, monitor your clipboard, and steal browser data once you execute their code or install their verification software.”
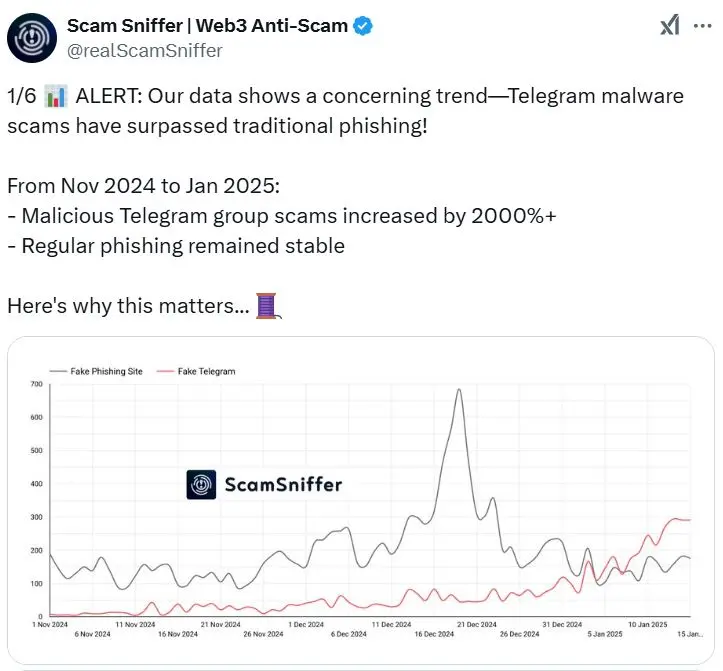
At least two fraudulent verification bots, OfficiaISafeguardRobot and SafeguardsAuthenticationBot, have been discovered by Scam Sniffer.
Fraud Sniffer claimed that as people have grown more conscious of signature scams, criminals have changed their strategies.
While losses are more difficult to track, malware provides attackers more access.
After observing a rise in scammers creating phony X profiles that mimic well-known cryptocurrency influencers and then inviting individuals to Telegram groups with promises of investment insights, the security firm first alerted the public about Telegram malware scams in December.
After joining the group, members are required to authenticate using a phony verification bot that infects computers with malware that steals private keys and raids cryptocurrency wallets.
In a different version, the malware is distributed via posing as Cloudflare verification sites, asking users to copy and paste the verification text, which surreptitiously inserts it into their clipboard.
Scam Sniffer said in an update on January 4 that scammers were now utilizing these techniques to attack legitimate project communities with “seemingly harmless invites,” going beyond simply posing as influencers.
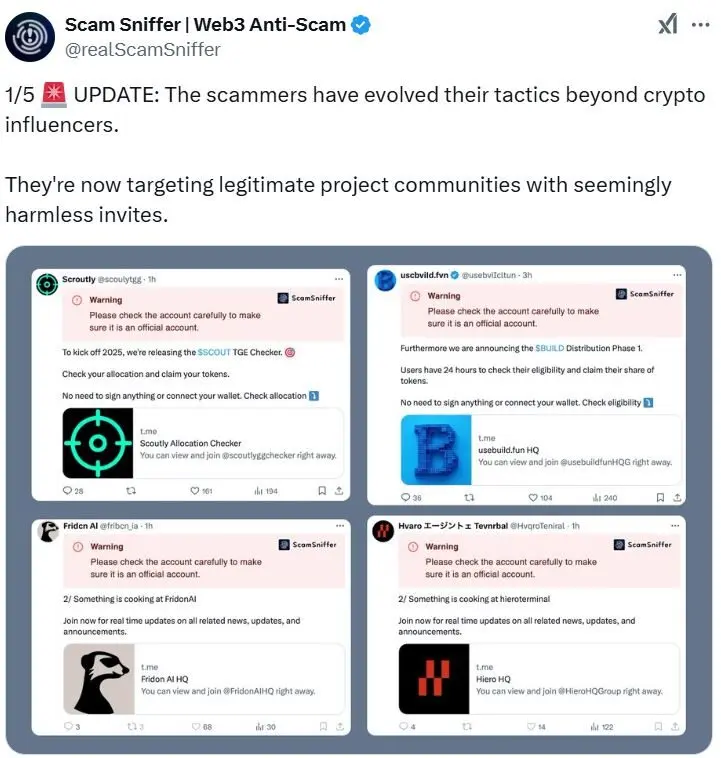
This change in strategy suggests that con artists are adjusting to users’ growing awareness of phishing links.
Rather, they’re using more advanced social engineering techniques with Telegram bots,” the security company stated.
Losses from malware attacks are often impossible to quantify.
However, the significant change in scammer strategies indicates that it is effective, the statement continued.
In December, Cado Security Labs issued a warning about a similar fraud, claiming that malicious actors were exploiting phony meeting apps to infect websites, apps, and cryptocurrency wallets with malware and steal login information.
According to the onchain security company’s Cyvers 2024 Web3 Security Report, which was sent to Cointelegraph on December 24, 165 instances totaling $2.3 billion in cryptocurrency theft occurred in 2024.
In comparison to 2023, when hackers stole $1.69 billion worth of cryptocurrency, Cyvers claims that this represented a 40% rise. Compared to the $3.78 billion that was taken in 2022, it is 37% less.
But according to two security companies, December witnessed the lowest annual losses from scams and cyberattacks, coming in at only about $29 million.



