Scammers exploited the hype around Uniswap’s new Ethereum Layer 2 by promoting a fake Google page claiming to support the network.
Erroneously, Google advertised a phony Unichain website that bombarded users with demands to empty their wallets.
Scammers have taken advantage of the excitement around cryptocurrency exchange Uniswap’s new Ethereum layer2 by promoting a phony page on Google that purports to support the network.
The website purported to be the official home of Uniswap’s Unichain network and was initially hosted at unlchalindefi[.]com. However, it could have provided a fresh network with approachable apps.
Rather, warnings displayed in the Web3 wallet MetaMask state that it took all of the user’s bitcoin and delivered it to the site developers, who had no connection to Uniswap.
The website was taken down as this piece was published, suggesting that its hosting provider may have learned about the scam and opted not to continue supporting it. However, the scam’s method highlights typical mistakes that Web3 users should avoid to protect their money.
The creator of Uniswap, Uniswap Labs, declared on October 10 that a testnet for “Unichain,” a forthcoming Ethereum layer 2 protocol, has been established. According to the release, the new network will eventually contain a block-building algorithm enabling transactions to “feel” as though they have been completed in 250 milliseconds. Furthermore, it will allow “seamless multichain swapping,” providing traders access to more liquidity and preventing slippage.
The statement that a Unichain mainnet would launch “later this year” was posted on the team’s official blog, Uniswap.org. Just a testnet was starting up right away.
Uniswap Labs also unveiled the official Unichain.org website for the new network on the same day as the announcement. However, the announcement of the more well-known blog post eclipsed this website over the following few days, preventing it from ranking well in Google search results for the keyword “Unichain.”
The con artists have recognized that the website’s deficiency in domain authority offered them a chance. They produced an identically mirrored duplicate of the website, with the exception that it had a “bridge” button in place of the “read the docs” button and a “connect” button where the “get started” button should have gone.
![Scammers Push Fake Uniswap L2 on Google - Protechbro: Top Stories on Bitcoin, Ethereum, Web3, & Blockchain Fake Unichain website. Source: unlchalindefi[.]com.](https://protechbro.com/wp-content/uploads/2024/10/image-54.png)
They then bought Google advertising, which enabled them to top Google search results for their website, but with a notice indicating that the website’s placement was “sponsored.” The advertisement included the URL for the official Unichain website, but clicking on it would take viewers to the phony website.
Afterward, Google took down this advert, moving the blog post back to the top of the search results. It’s possible that many found the scam more challenging to detect, especially if they were pressed for time because the legitimate Unichain website was not displayed in search results during this period.
On October 15, Scam Sniffer, a blockchain analytics tool, uncovered and reported the misleading search results on X.
Reporters for Cointelegraph used an empty wallet to test the fraudulent website and app. The website requested a wallet connection in the customary way once you hit “connect.” However, as soon as the connection was authorized, the website bombarded the user with requests for transaction confirmations. If the transaction was declined, the website promptly returned the transaction to the wallet. Closing the tab in the browser was the only method to get rid of the spam.
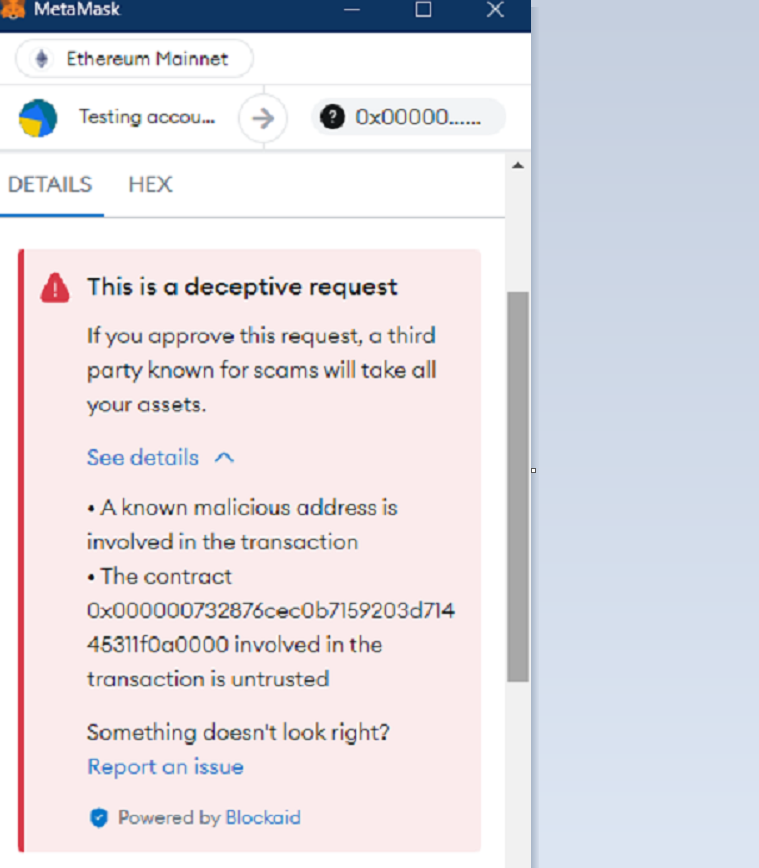
Every transaction connected through MetaMask had a warning from Blockaid: “This is a deceptive request.” A third party with a history of scams will seize your assets if you grant this request.
It’s conceivable that the con artists were unsuccessful in emptying any wallets this time around because the fraud seems to have been immediately taken down. However, the method shows how simple it is for Web3 users to lose money.
Generally speaking, Web3 users should avoid clicking on Google adverts for protocols since these are frequently scam sites that have passed the search engine’s censors. Furthermore, while they engage with a new web application, users should consider closely reviewing transactions to ensure they comprehend what they are allowing, as con artists sometimes rely on people carelessly clicking “confirm.”
An address ending in a0000 was the target of a function call that the fraudulent transaction attempted to make. It is hazardous to deal with this account because it has interacted with multiple accounts that Etherscan has classified as “Fake_Phishing.”
Based on its documentation, Unichain is just at the testnet stage of development. According to this, users can only transfer money to it from other tenets, such as Sepolia. Most likely, any website that claims that users can bridge from a mainnet to Unichain right now is a hoax.
Uniswap stated that end users should be able to bridge their assets from other networks onto the mainnet by the time it launches “later this year.”
Notwithstanding Google’s ongoing efforts to create more robust filters to thwart scammers, Google advertisements for phony protocols have consistently presented a risk to Web3 users. According to research published by Scam Sniffer in December, attackers used this method to siphon up almost $59 million from customers in just nine months.



