Personal security threats in crypto’s bull market are increasing rapidly. With expert tips and tools, you can stay safe in 2025 by preventing phishing, SIM swaps, malware, and wallet drainers.
Why Bull Markets Attract Security Threats
Crypto bull markets are periods of rapid price appreciation and increased trading activity, but they also bring a wave of sophisticated security threats.
As token valuations rise, so does the motivation of malicious actors. Understanding the psychology and patterns that drive these attacks is critical to safeguarding your assets.
1. Increased Activity = Higher Target Value
During bull runs, blockchain networks experience a surge in on-chain activity, wallet creation spikes, DeFi protocols attract more users, and NFT marketplaces expand rapidly.
This influx of participants, particularly newcomers with limited security knowledge, presents an opportunity for scammers. As average wallet values rise, attackers find it more profitable to target even casual users.
According to Chainalysis, more than $1.7 billion was lost to crypto scams in 2024 alone, and the trend is expected to worsen during the current bull market.
2. Public Displays of Wealth Invite Threats
Social media platforms such as Twitter (now X), TikTok, and Discord are flooded with users sharing screenshots of trading profits, rare NFTs, or wallet achievements. While this increases excitement, it also paints targets on their backs.
Cybercriminals use these platforms to identify individuals to target via social engineering, phishing, or SIM swapping.
Flexing wins during a bull run is not just vanity; it serves as a beacon for threat actors.
3. Exploiting FOMO and Hype-Driven Behavior
Bull markets are emotionally charged. Investors rush into trending tokens, hyped launches, and meme coins, frequently skipping due diligence.
Scammers take advantage of this urgency by distributing fake airdrops, phishing links disguised as “early access” portals, or impersonating influencers to promote malicious contracts.
This provides an ideal environment for crypto phishing attacks in 2025, especially as AI-generated fake messages and deepfakes become indistinguishable from legitimate communication.
4. False Sense of Security
A prolonged bear market typically results in cautious behavior. As assets increase in value, users may become relaxed and assume all platforms and projects are legitimate.
This complacency makes them more vulnerable to sophisticated exploits like drainer contracts and wallet approval manipulation.
Bull markets in crypto attract increased security threats due to increased wallet values, user activity, and emotional decision-making. As prices rise, scammers use public displays of wealth and investor FOMO to launch targeted attacks such as phishing, fake airdrops, and wallet drainers.
Even experienced users are vulnerable in this hype-driven environment, especially as AI-powered impersonation tactics become more prevalent. Stay vigilant as crypto scams in bull markets and phishing attacks become more sophisticated and widespread in 2025.
Recognizing the Most Common Personal Security Threats
As crypto adoption increases in 2025, so do the methods used by malicious actors. Understanding how these threats operate is the first step in preventing them. The following are the most common personal security risks in today’s crypto bull market.
1. Phishing Attacks and Fake DApps
One of the most common crypto scams involves phishing websites that mimic popular wallets or dApps. These sites prompt users to connect their wallets or enter their seed phrases, resulting in immediate asset theft.
Airdrop scams are especially common during bull runs, when users are tricked into connecting their wallets to fake “claim” portals. Similarly, wallet pop-ups created by malicious browser extensions can trick users into signing harmful transactions.
2. SIM Swaps and Account Takeovers
Crypto SIM swap attacks in 2025 are on the rise due to social engineering tactics aimed at mobile carriers. By fraudulently porting your phone number, attackers can bypass two-factor authentication (2FA) and gain access to your crypto exchange or wallet apps.
Major exchanges, such as Coinbase and Binance, have reported an increase in SIM swap-related account breaches in recent months, emphasizing the importance of using authenticator apps rather than SMS.
3. Malware/Keyloggers
Attackers are using more sophisticated malware, which is often hidden in pirated software or fake wallet apps. Once installed, these programs monitor clipboard activity, waiting for you to copy a wallet address before silently replacing it with their own.
Other types of malware include screen recorders, keyloggers, and browser hijackers, which capture private keys, passwords, and transaction approvals in real time.
4. Social Engineering Scams
Scammers use platforms like Telegram, Discord, and LinkedIn to impersonate trusted figures such as crypto influencers, founders, or customer support agents. Some use deepfake videos or AI-generated voices to make interactions appear authentic.
Victims are often deceived into sending funds, sharing login information, or clicking malicious links under the guise of technical assistance or giveaways. Fake support crypt fraud is especially prevalent in high-traffic communities during bull markets.
5. Drainer Smart Contracts
One of the most dangerous and difficult-to-detect threats is the wallet drainer scam. Malicious smart contracts can drain all tokens from a wallet if a user unknowingly grants access. These contracts are often embedded in fake NFT mints, DEX launches, and airdrop platforms.
Drainer contracts, unlike phishing sites, can appear legitimate transactions, making them difficult to detect for non-technical users.
In 2025’s bull market, crypto users face an increasing number of sophisticated threats. Phishing sites and fake dApps trick users into disclosing their seed phrases, whereas wallet drainer scams use malicious smart contracts to empty wallets instantly.
In 2025, crypto SIM swap attacks target mobile carriers in an attempt to bypass 2FA and hijack accounts. Meanwhile, malware such as keyloggers and clipboard hijackers quietly collect sensitive information.
Social engineering scams, such as fake support crypto fraud, take advantage of people’s trust in influencers and support agents. Recognizing these risks is critical to protecting your digital assets.
Proactive Steps to Protect Yourself
As personal security threats in the crypto bull market become more sophisticated, protecting your assets requires a proactive mindset. Here are four key steps that every user should take to reduce risk:
Use Hardware Wallets for Long-Term Storage
Cold wallets, such as Ledger, Trezor, and Keystone, provide the most secure way to store your crypto, especially during volatile bull markets.
Unlike hot wallets, hardware wallets stay offline, protecting your private keys from online threats such as malware, wallet drainer scams, and phishing sites.
To remain protected:
- Purchase directly from the manufacturer to avoid tampered devices.
- Maintain regular firmware updates to address vulnerabilities.
- Store seed phrases offline and never type them into a browser.
Enable Multi-Factor Authentication (MFA)
Avoid relying solely on email or SMS for logins. Instead, secure your exchange accounts and wallets with app-based MFA tools such as Google Authenticator, Authy, or Yubikeys.
MFA provides an extra layer of security by requiring a one-time code or physical token to complete logins, even if someone knows your password. This is crucial for preventing crypto SIM swap attacks in 2025.
Don’t reuse MFA credentials across platforms.
Avoid Clicking Links from Social Media or Email
Bull markets are an ideal time for scammers to spread malicious links via Twitter (X), Telegram, Discord, and email. These links frequently direct to fake crypto support sites, phishing portals, or drainer smart contracts.
Stay safe by:
- Manually typing URLs or using saved bookmarks.
- Ignoring unsolicited DMs and support messages.
- Verifying domains with tools like Chainabuse and ScamSniffer.
Check All Smart Contract Permissions
Approving a malicious contract can give hackers complete access to your tokens, even if your seed phrase is secure. Regularly audit your wallet’s permissions with tools such as:
- Etherscan’s Token Approval Checker
- Revoke.cash
Revoke access to dApps that you no longer use, and never allow unlimited token spending unless absolutely necessary.
To stay safe during the crypto bull market, use hardware wallets for secure storage, enable app-based MFA, and avoid clicking on suspicious links.
Regularly revoke smart contract permissions with tools such as Revoke.cash and Etherscan. These proactive measures reduce your vulnerability to wallet drainer scams and crypto security threats.
Tools and Platforms that Enhance Personal Security
As the personal security threats in the crypto bull market grow, using specialized tools can significantly reduce your vulnerability to scams, malware, and wallet drainers. Here are some of the most effective tools for crypto wallet security and DeFi protection:
1. MetaMask with Built-in Phishing Detection

MetaMask, a leading DeFi wallet, has integrated phishing detection features that warn users when they connect to suspicious sites. While not perfect, it can help users avoid fake airdrop pages or drainer smart contracts during transaction approvals.
To improve threat detection, make sure MetaMask is always updated to the latest version.
2. Wallet Guard, Rabby Wallet, and Fire Extension
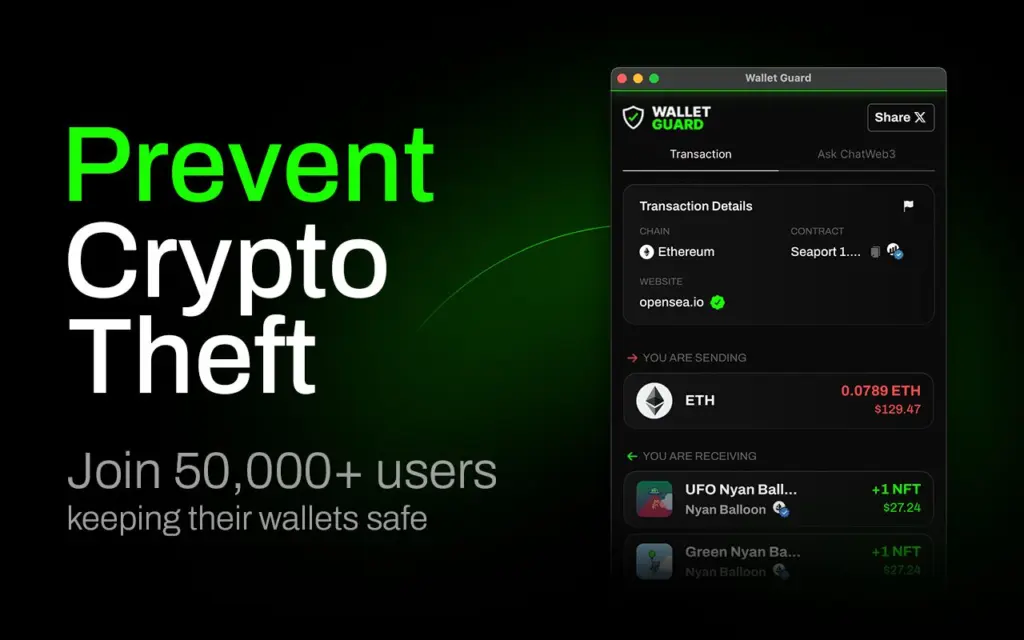
These browser extensions serve as security layers on top of Web3 wallets:
- Wallet Guard scans malicious transactions and phishing links in real time.
- Rabby Wallet (by DeBank) displays the permissions that a smart contract is requesting before you approve it.
- Fire Extension simulates transactions in detail and alerts you to any red flag activity.
These are essential for anyone who actively uses DeFi platforms.
3. Revoke.cash and DeBank
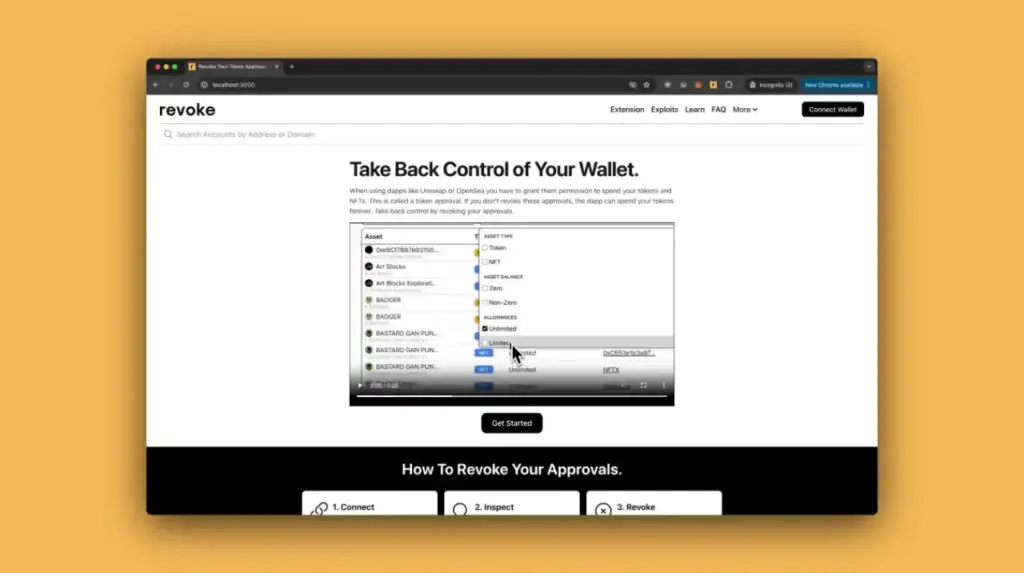
Token approvals allow dApps unlimited access to your assets. Revoke.cash and DeBank enable you to:
- View all granted smart contract permissions.
- Revoke outdated or risky approvals.
- Monitor wallet activity across chains.
Using these tools on a weekly basis can help prevent wallet drainer scams and stealth token theft.
4. Google Advanced Protection Program (GAPP)

Crypto users who use Gmail for exchange logins or wallet recovery should enroll in GAPP, which:
- Apps that have not been verified are blocked
- Requires security keys for login
- Enhances phishing protection for high-risk accounts.
This is critical for preventing SIM swaps and account takeover attacks.
5. Chainabuse and Scam Sniffer
- Chainabuse allows you to report and search for scam wallet addresses on multiple blockchains.
- Scam Sniffer provides real-time alerts for dangerous contracts and fake websites, which are frequently used in phishing attacks or impersonation schemes.
These tools are community-driven and can quickly expose bad actors.
Protecting your crypto assets in a bull market requires the right tools. To ensure safe DeFi interactions, use MetaMask with phishing detection, Wallet Guard, and Rabby. Revoke.cash and DeBank provide tools for monitoring and revoking smart contract approvals.
Enhance account security with Google Advanced Protection, and report scams with Chainabuse or Scam Sniffer. These tools are critical for crypto wallet security and DeFi protection in 2025.
Behavioral Tips to Stay Safe During the Bull Market
In a bull market, hype can cloud judgment, which is exactly what scammers rely on. Along with using secure tools, your personal habits are critical in staying safe. Here are important behavioral strategies for strengthening your crypto OPSEC in 2025:
1. Avoid Public Bragging of Gains or NFTs
Publicly displaying profits, rare NFTs, or large wallet balances on X (Twitter), Telegram, or Discord can make you a prime target.
Criminals use social media to identify high-value targets for phishing, SIM swaps, and even physical threats. Privacy equals security; the less you reveal, the safer you are.
2. Don’t Sign Transactions You Don’t Understand
Malicious smart contracts are now being disguised as legitimate DeFi opportunities. If a dApp or prompt asks you to sign a transaction that you don’t fully understand, do not proceed. When in doubt, pause and confirm.
Many wallet drainer scams take advantage of users’ impatience or lack of knowledge during periods of FOMO.
3. Rotate Wallets and use Burner Wallets for DeFi
Keeping all of your assets in a single wallet is risky. Consider rotating wallets for various purposes (staking, trading, and holding), and always use a burner wallet when interacting with new or experimental dApps. This helps to reduce exposure if one wallet is compromised.
Your seed phrase holds the ultimate key to your funds. Store it in multiple secure spaces (for example, metal backups or encrypted offline storage). Never upload it to the cloud, take screenshots, or send it to anyone; no legitimate support will ever request it.
Adopting these behaviors will significantly reduce your risk while others fall victim to hype-driven schemes. Learning how to stay safe during bull market crypto cycles is equally important as riding the next wave of gains.
What to Do If You Suspect a Breach
If you suspect that your wallet or crypto account has been compromised, take immediate action to minimize your losses. Here are the necessary steps to take:
1. Disconnect and Revoke Access Immediately
Use platforms like Revoke.cash or DeBank to revoke smart contract permissions. Disconnect your wallet from all websites and DeFi platforms to prevent potential exploit scripts.
2. Transfer Remaining Funds to Cold Storage
Quickly transfer any remaining assets to a hardware wallet or a new, uncompromised address. This reduces vulnerability to future attacks or drainer contracts.
3. File a Report on Chainabuse or with Your Exchange
Document the breach and report it to Chainabuse, a community platform that tracks crypto scams. Also, notify your centralized exchange (CEX), if applicable, especially if fiat ramps or KYC are in place.
4. Change All Passwords and Secure Recovery Emails
Update your email, wallet, and exchange passwords. Utilize multi-factor authentication (MFA) with an app-based authenticator. Make sure your recovery email accounts are secure and protected with programs like Google Advanced Protection.
5. Report to Law Enforcement or National Cybercrime Units
If you are a victim of theft or a large scam, you should file a cybercrime report with your country’s financial or digital crime unit. Some cases may be traceable using blockchain forensics.
These steps are vital for anyone attempting to recover a hacked crypto wallet or report crypto scams in 2025. Acting quickly can make the difference between total loss and partial recovery.
Conclusion
The bull market unlocks huge opportunities, but it also attracts sophisticated threats that target unsuspecting users. From phishing schemes to wallet drainers, the risks increase as prices rise.
Security in Web3 is more than just having the best tools; it is also about developing a security-first mindset. Regularly update practices, be wary of hype, and never rush into transactions you don’t understand.
Finally, being proactive with personal protection is the most reliable way to remain profitable and safe in the ever-changing landscape of the crypto bull market.



