It is believed that North Korean hackers were responsible for the $235 million hack of the Indian cryptocurrency exchange WazirX.
Serious concerns concerning exchange security and the future of cryptocurrencies in India were expressed after the $235 million attack on the Indian cryptocurrency exchange WazirX on July 18.
The assault developed with startling accuracy and speed, and Web3 security company Cyvers was one of the first to identify “multiple suspicious transactions” involving WazirX’s Ethereum “Safe Multisig” wallet.
With the use of assets from bitcoin mixer Tornado Cash, the attacker was able to transfer an astounding $234.9 million in money to a new address.
Among the stolen monies, various cryptocurrencies, including Tether USDT$1.00, Pepe PEPE$0.000012, and Gala GALA$0.03, were among the cryptocurrencies. The attacker quickly converted these assets into Ether ETH$ 3,499 to hide the trail of stolen funds.
Along with smaller quantities of other tokens, the exchange’s wallet had about $100 million in Shiba Inu (SHIB$0.000018), $52 million in ETH, $11 million in Polygon (MATIC$0.5432), and other tokens.
WazirX instantly stopped allowing withdrawals of Indian rupees and cryptocurrencies from the platform due to a security issue. Additionally, it was said in the conversation that it was “actively investigating the incident.”
WazirX spokesperson Rajagopal Menon told Cointelegraph that the company could not comment on the circumstances. Updates are available via our Twitter account.
The crypto industry’s prospects in India
The attack may significantly impact India’s cryptocurrency market, which has thrived in defiance of government pressure.
Chief strategy officer of the Indian cryptocurrency exchange KoinBX, Utkarsh Tiwari, told Cointelegraph that a breach of this size in terms of security is sure to raise concerns because it impacts several parties in the crypto ecosystem, such as other exchanges and retail investors. He continued, saying:
“Under India’s G20 presidency, we have seen our government push for comprehensive and standardized regulations for all global Virtual Assets Service Providers. Furthermore, historically, we have seen the Indian government always prioritize investor protection above all else.”
Tiwari believes that this would lead to an increase in investment by Indian digital asset exchanges in sophisticated security infrastructure, which will assist in highlighting the market’s and the community’s resilience and inventiveness.
The cryptocurrency market in India hopes that the strict tax laws governing cryptocurrency in the nation will soon ease.
The cryptocurrency industry anticipates positive improvements when India’s Finance Minister, Nirmala Sitharaman, presents the Union Budget for the upcoming fiscal year on July 23.
India has had one of the harshest cryptocurrency tax policies in the world since 2022. Profits from digital assets, including non-fungible tokens, are subject to a fixed 30% capital gains tax. Crypto transactions additionally incur a 1% tax deducted at source (TDS).
The CEO of the Indian cryptocurrency exchange CoinDCX, Sumit Gupta, has been pushing for the upcoming budget to lower the TDS rate to 0.01% because these tax changes have greatly influenced Indian cryptocurrency exchanges.
How did the attackers obtain WazirX?
Web3 security company Cyvers’s chief technical officer and co-founder, Meir Dolev, told Cointelegraph that although the exploited vulnerability is still unknown, several vital details have come to light since the incident.
To begin with, he mentioned that WazirX employs a multi-sig wallet, which requires four signatures to complete a transaction. In addition, Liminal serves as the exchange’s custody provider, providing the final signature for each transaction. Last, due to its allowlist policy, WazirX’s wallet can only send money to a few wallets.
Dolev described the attack vector: “The attacker used two separate addresses, one that started the transaction and the other that received the funds. The person who started the transaction wanted to pay for gas, so he used Tornado Cash to fund his wallet.
“Eight days before the attack, the hacker also deployed a malicious contract that was later used to change the implementation of the WazirX wallet.”
He said the attacker used WazirX’s and Liminal custody’s signatures to modify the multi-sig wallet’s implementation to his malicious contract just minutes before the first exploit transaction. He emphasized, “From that point on, he could complete any transaction without requiring WazirX or Liminal to sign on the transaction.”
Dolev surmised that the attacker most likely broke into WazirX endpoints or laptops to obtain the required signatures, maybe by using a user interface (UI) hijack on Liminal’s end.
According to him, WazirX may have believed they were about to sign a valid transaction based on what was observed in the user interface, presumably under the hacker’s control.
“We can confirm that Liminal’s platform is not breached, and Liminal’s infrastructure, wallets, and assets continue to remain safe,” said Liminal Custody, despite initial investigations indicating that one of the self-custody multi-sig smart contract wallets established outside of the Liminal ecosystem was compromised.
Suspicion of North Korean participation
To an already complicated situation, many specialists speculate that North Korean hackers could have been behind the incident, adding another level of geopolitical intrigue.
Data suggested North Korean involvement, according to blockchain forensics company Elliptic, which earlier confirmed this to Cointelegraph. Elliptic said, “The North Korea attribution is based on analysis of the on-chain transactional behavior and other information.” This kind of performer uses particular patterns and strategies that are distinctive to them.
ZachXBT agreed, stating that the hack has similarities to an attack by the notorious Lazarus Group, a North Korean criminal group with a lengthy history of cybercrime.
Lazarus has haunted the cryptocurrency world since 2017 and is said to be responsible for some of the greatest scams in the business, such as the $650 million Ronin Bridge affair.
Furthermore, there was significant volatility in the cryptocurrency market following the attack. The breach saw the theft of SHIB tokens valued at over $100 million, which sent the price of the well-known memecoin plunging by 10%.
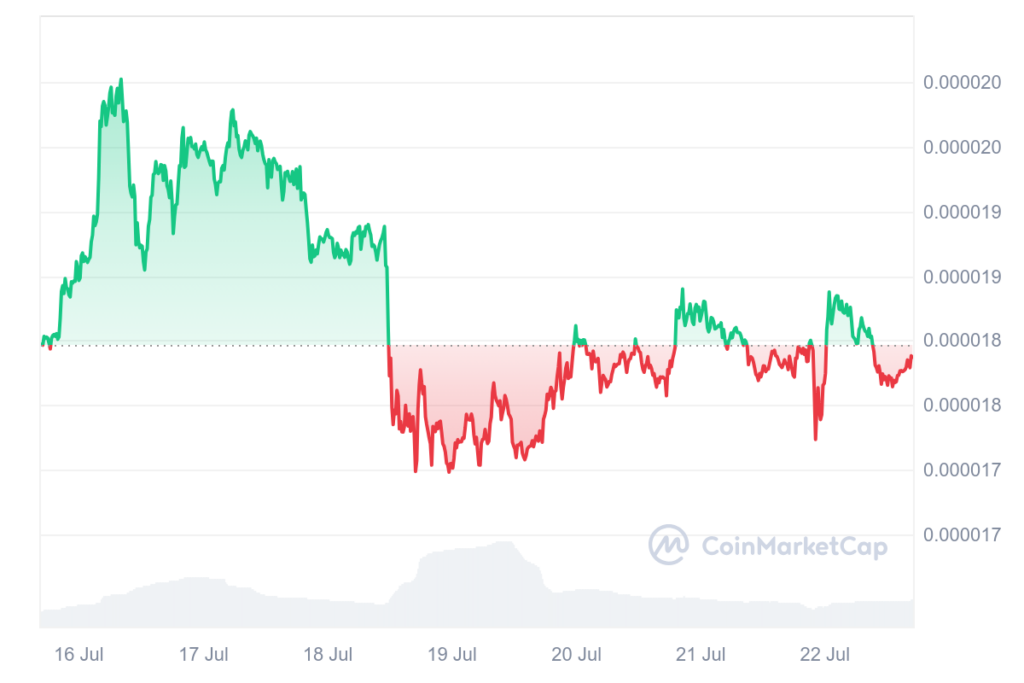
One day after the incident, on July 19, the blockchain analysis platform Lookonchain revealed that the attackers had started exchanging SHIB assets for ETH, selling 35 billion SHIB tokens for $618,000. Most assets had been traded for 43,800 ETH ($149.46 million), and the exploiter now owned 59,097 ETH ($201.67 million).
WazirX has moved quickly to repair the harm and get the stolen money back. The exchange explores further legal action and the filing of a formal police report.
It contacts more than 500 exchanges to block the detected addresses after reporting the matter to the Indian Computer Emergency Response Team and the Financial Intelligence Unit.
The exchange said, “We are actively working with many exchanges on additional resources to aid in our recovery efforts, and many of them are cooperating with us.”



