According to research by Roffet.eth, some memecoins had cryptic, hard-to-read code that lets the creator take user tokens and keep them for themselves.
According to a Sept. 25 X post from security researcher Roffett.eth, scammers are luring unwary customers and stealing their cryptocurrency by utilizing a “trending” list on memecoin analytics site GMGN.
The developers can transfer any user’s tokens to themselves thanks to the coins the attackers make. After that, they exchange the token between several accounts, creating a false volume and adding it to the “trending list” on GMGN.
Unaware consumers purchase the coin, thinking it is well-liked after it appears on the trending list. However, their coins vanish from their wallets in minutes and are never seen again. After that, the developer sells the coin to a different victim and redeposits it into its liquidity pool.
Billy’s Dog (NICK), DFC, and Robotaxi were three instances of harmful coins that Roffet identified in the list.
An analytics web application called GMGN serves traders of memecoins on Base, Solana, Tron, Blast, and Ethereum. Its interface is divided into multiple tabs, such as “new pair,” “trending,” and “discover,” which list coins according to various standards.
After friends bought coins from the list and noticed that they had inexplicably vanished, Roffett says he figured out the fraud tactic. One friend thought his wallet had been compromised, but he couldn’t get the coins back even after creating a new wallet and buying them.
Captivated by the enigma, Roffett used a block explorer to investigate the attacks and discovered they were like standard phishing attempts. The attacker provided the user’s signature via a “permit” function, which shouldn’t have been conceivable unless the victim had fallen for a phishing scam. The friend refuted claims that he had visited dubious websites before the two attacks.
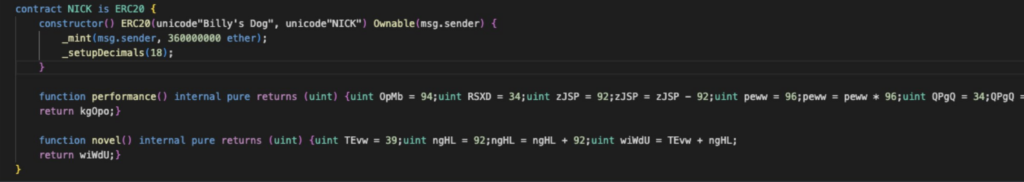
NICK was one of the stolen coins. After looking at NICK’s contract code, Roffet discovered it was “somewhat strange.” This token contract featured “some very odd and obfuscated methods” instead of the typical stock code seen in most token contracts.
Roffet shared a picture of NICK’s “performance” and “novel” functions, which include cryptic language with no apparent use, as proof of these peculiar techniques.
Roffett eventually found that one of the contract’s libraries included malicious code. By using this code, the “recoverer” (developer) was able to use the “permit” method without having to supply the tokenholder’s signature. According to Roffett:
“If the caller’s address equals the recoverer, then by constructing a specific signature manually, one can obtain the permit permission of any token holder and then transfer the tokens.”
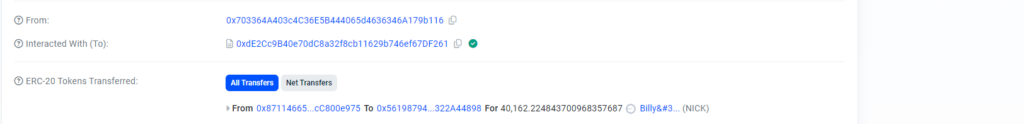
But the address of the recoverer was also hidden. It was described as a positive, non-zero, 256-bit integer. The function that the contract utilized to determine the address from this number was located just below this number. Roffett employed this feature to ascertain that the malevolent “recoverer” was a contract with an address that concluded in f261.
According to blockchain statistics, this “recoverer” contract has moved over 100 NICK tokens from the token holders to different accounts.
After learning how this scam operated, Roffett looked into the “trending” list and realized that DFC and Robotaxi were at least two other tokens with similar codes.
Roffett concluded that con artists had most likely used this method for a while. He cautioned users against using this list because doing so could cause them to lose money. He said:
“Malicious developers first use multiple addresses to simulate trading and holding, pushing the token onto the trending list. This attracts small retail investors to buy, and eventually, the ERC20 tokens are stolen, completing the scam. The existence of these trending lists is extremely harmful to novice retail investors. I hope everyone becomes aware of this and doesn’t fall for it.”
Crypto users are still at risk from scam tokens, sometimes called “honeypots.” A scam token developer defrauded victims out of $1.62 million in April by offering them an unsellable BONKKILLER token. Over 350 scam currencies were formed in 2022, according to research published by blockchain risk management company Solidus.